The latest update now protects from known YouTube Live trust-trading scams.
TL;DR: EtherAddressLookup v1.23 has launched and protects from known malicious YouTube livestreams that advertise trust-trading scams and bad publications on the telegra.ph domain (which have been becoming more and more common recently).
Back in 2017, just at the start of the “crypto bull run and ICO craze,” I published a browser extension that helped protect users from known phishing domains — the first browser extension that focused on protecting users, for free, from known cryptocurrency scams — and it got a lot of attention!
Since that time, we’ve seen how phishing kits evolved and techniques improved to try and get honest users to part with their cryptocurrency — and we’ve written about a lot of campaigns to help the community protect themselves.
To refresh your memory, here’s a brief, scattered timeline of campaigns that we’ve monitored, helped take down, and helped educate users about:
- Slack groups hijacked by Slackbot reminders to push phishing domains to users during the ICO craze — https://twitter.com/sniko_/status/899348939341778945
- Modified wallet interfaces using punycode and misspelled domains to trick users into inputting their raw secrets that were sent to the backend — https://twitter.com/sniko_/status/1047814865820237825
- Fake airdrop sites that phished users’ secret keys by asking them to sign a message to prove ownership of their address to get free $xxx in tokens — https://twitter.com/sniko_/status/928314103625650176
- Massive effort in hijacking DNS/BGP routes to redirect legitimate domains to malicious servers with malicious code to steal users’ funds — https://twitter.com/epatryk/status/988827484098584578
- Malicious APK apps being published on third-party directories to phish for users’ secrets — https://twitter.com/sniko_/status/1202803912186699783
- Takeovers of social media “influencers’” accounts to push trust-trading scams — both via DMs and via websites — https://twitter.com/sniko_/status/983061114824155136
- Takeovers of YouTube accounts to run pre-recorded video via livestream to push trust-trading scams and malicious wallet interfaces to steal secrets — https://twitter.com/sniko_/status/1006179572637929472
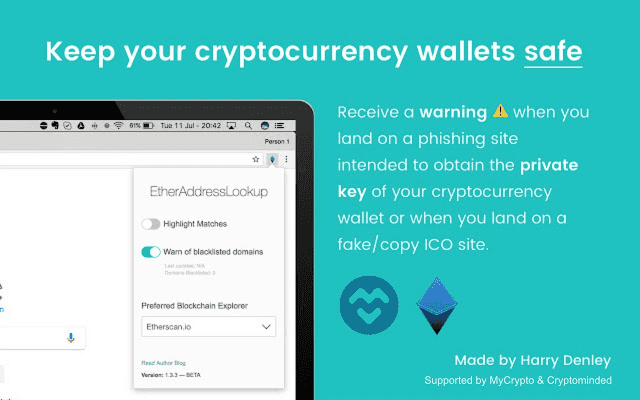
EtherAddressLookup was initially launched to tackle the influx of phishing domains in near-real-time without relying on third-party services, such as GoogleSafeBrowsing or PhishTank, to take time to verify and categorise bad domains. EAL allowed maintainers (people that the community trusted) to act fast and quickly push a malicious domain to the EAL blacklist to prevent a user running the browser extension (at the peak this was 120,000 cryptocurrency users) and interacting with the known bad domain — and it was effective!
EtherAddressLookup is different from other browser extensions that do similar jobs at protecting users. Instead of hitting a third-party server for every domain you browse, we store all the blacklists and whitelists locally (via LocalStorage on the extension). We don’t care for your browsing history or to fingerprint you in any way — only to protect you from known bad domains. You can read more on the published privacy policy. We also keep dependencies to a minimum so you don’t have to worry about another event-stream incident, and we are 100% open source (even our latest version is auditable) so you can audit the code as well as manually load the version you want.
The new update
With this new update, EtherAddressLookup will still be able to prevent you from interacting with bad domains, but also bad paths — this means we can now protect you from known malicious YouTube livestreams that advertise trust-trading scams and bad publications on the telegra.ph domain (which have been becoming more and more common recently). You can see our blacklist here.
If you already have EtherAddressLookup installed, you don’t need to do anything*.
If you want to install EtherAddressLookup, please see the product page to get instructions on how to install it from the Google Chrome store and how to install it manually.
(* if you have installed it manually, then download the latest tag and reload the extension. If you installed it from the Google Chrome Store, you should have it automatically updated — make sure you’re running v1.23)
Just like our other blacklists, we will be keeping this list up-to-date with anything that we find that has malicious intent to separate you and your cryptocurrency.
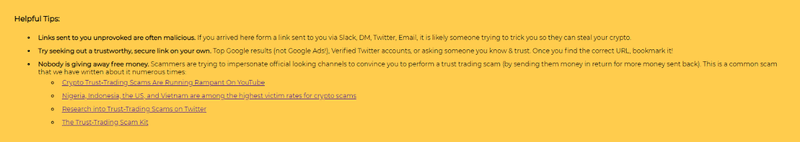
In this update, we have also added a helpful tip to the warning view to remind you on how to stay safe against one of the most common scams.
We don’t just stop at blacklisting! We also have a couple of bots running in the background and communication lines with select companies on our data feeds so we can get a better idea on:
- Where stolen funds are routed
- The infrastructure running the scams
- Fingerprinting phishing and scam kits
- How the kits work, so we can help educate the community
Awesome, I want to contribute!
If you find a live stream or an article that is malicious, then please open a PR to blacklists/uris.json file (or report via CryptoScamDB), and once merged, everyone should be prevented from seeing the malicious content within ~10 minutes (as caches refresh).
We also run everything via urlscan.io and then have bots to backup data to an S3 bucket so we can do some analysis later — big shoutout to URLScan for having such a great service! We also run a passive hunter (punter) on infrastructure found in blacklists/domains.json to build our infrastructure map to find more domains.
If you’d wish to contribute to the antiphishing work, we have a tip jar that supports ETH & ERC20 donations at 0x661b5dc032bedb210f225df4b1aa2bdd669b38bc.
Thank you for the support!