You are harming your users and the ecosystem when you allow people to enter their private keys, keystore files, or secret recovery phrases on your website.
Let’s Start With The Basics
What is a private key?
Every account consists of two parts: a public key and a private key.
The public key is your public address (sort of) and you can share this with your friends so they can send you ether. It’s similar to your email address or postal address.
The private key is the method of accessing the assets stored in an account. This is the piece of information that cryptographically proves you are allowed to send these assets. It’s similar to the password to your email account, or the key to your mailbox.
What’s the difference between a private key, keystore file, and a secret recovery phrase?
A keystore file is a file that is generated using your private key + a password of your choosing. Using fancy math and code…
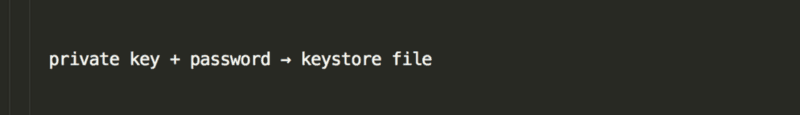
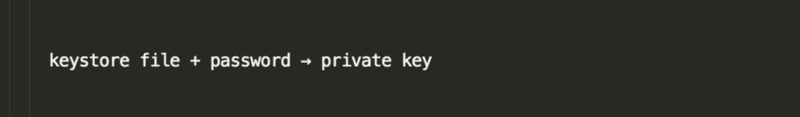
If you only have the keystore file (without the password), you cannot “go backwards” to get the private key. However, if you combine the password with the keystore file, you can use fancy math and code…
A secret recovery phrase, previously known as a mnemonic phrase, is actually a whole bunch of private keys, represented by a 12- or 24-word phrase that looks something like brain surround have swap horror body response double fire dumb bring hazard. Again, using fancy math and code…
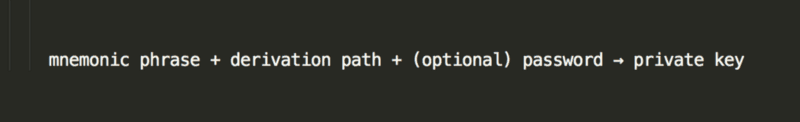
The derivation path is a numerical representation of which private key/address you wish to access. Have you ever had trouble accessing your older Ethereum addresses when you use Ledger Live? The derivation path is why.
Unlike a keystore file, there is no way to turn a private key into a secret recovery phrase. It’s a one-way street.
To summarize:
Secret recovery phrases turn into private keys, and keystore files turn into private keys. They’re all private keys, just different names/methods.
We’re going to refer to this whole collection of methods as “private keys” from here on out.
How is my private key used to access my account?
Because the blockchain is distributed, all the different computers and miners and nodes around the world have to play by the same defined set of rules and agree on the “state” of the blockchain at every point in time. For example, they all agree on what each account balance is, when a certain amount of ETH was sent, where it was sent to, etc.
To prevent just anyone from sending any assets from any account, there has to be a way to identify who the sender is and verify that they are allowed to send from a given account. This is done via cryptography (aka fancy code and math 😉).
When you send a transaction you take all the information about the transaction (the amount you want to send, the address you are sending to, the amount of gas, etc.) and then you sign it using your private key to prove that you are allowed to send that transaction:
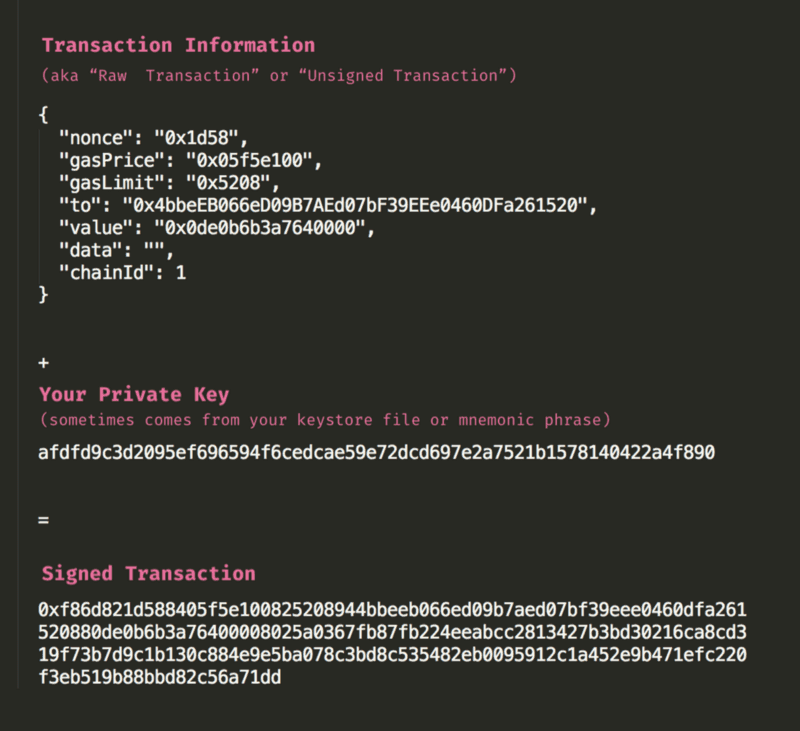
You do not send your private key anywhere, but all of the nodes and miners can use cryptography to quickly and easily verify you have the authorization to send that transaction. Again, fancy math and code.
How do I traditionally access my accounts?
If you’ve used the internet, you’re familiar with the idea of logging into a site or application with a username (or email address) and password. You may additionally provide a 2FA code.
When you do this you send your email and password to the central server; that server checks whether it is valid (the same as the information they have stored on their server), and either grants you access or denies you access.
P.S. You can learn more about how 2FA works here.
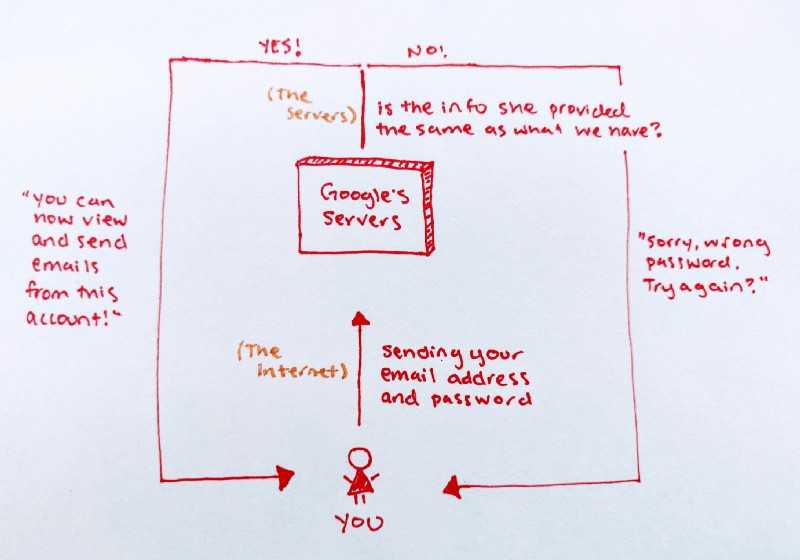
Because the methods used for traditional authentication via a central server are fundamentally different than the method used to authenticate a transaction on the blockchain, there are some key differences you should be aware of:
You don’t need a username and a password, just the single private key.
When sending your ether, you’re not required to have both the public and private keys. All you need is a private key to gain access to a wallet. This creates additional risk, as a scammer or phishing site only needs to obtain that one piece of information to ruin your day/month/year/life.
There’s no “forgot password” button.
If you ever lose your private key, there’s nothing that can be done. Because your private keys are not stored on a central server (like your username + passwords traditionally are), there is no one to recover it for you. If you lose it, it’s gone and your assets are forever unrecoverable.
There’s no two-factor authentication.
If someone gains access to your private key, the only thing you can do is hope you’re faster at moving assets than they are. There’s no 2FA to ensure that your key is behind another layer of protection. If you lose it, you lose it.
There’s no insurance if you do screw up. No reversing transactions.
This is true for all of cryptocurrency, but it highlights the significance of keeping your keys safe (and not typing/pasting them into a browser). If someone gets a hold of your private key and sends your funds elsewhere, there’s nothing you can do.
There is no way to change your private key.
Because all the nodes and miners all across the entire world have to play by the same cryptographic rules, there is no way to change your private key to prevent further loss once your account is compromised.
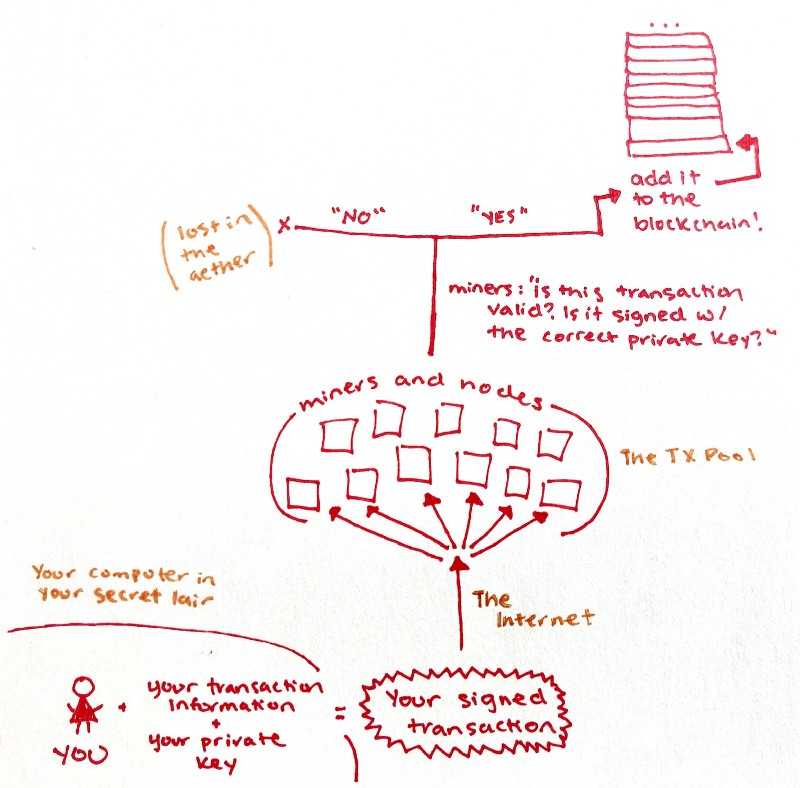
What should we do about it?
A personal note from Taylor:
When we first started building MyEtherWallet (and now MyCrypto), I didn’t realize how dangerous it was to encourage people to use their private keys on a website. I figured if we were trustworthy and we never sent the private keys anywhere, then it would be safe.
That was shortsighted, stupid, ignorant, harmful and we can never go back in time to change the decisions we made in early 2015.
Regardless of all the good, we are responsible for not only encouraging our users to engage in a terrible practice, but also encouraging other developers, products, and companies to follow our lead. This has resulted in more loss than I can comprehend.
According to our stats at CryptoScamDB, over 40,000 ETH has been sent to addresses that are flagged as being affiliated with scams or phishing sites. Those are just the ones targeting individuals — that doesn’t include attacks on exchanges and companies. (see this data via Dune Analytics)
No amount of education, 10-page onboarding pop-ups, checkboxes, screaming, nor stomping our feet will prevent users from taking the easiest path. If you allow them to use their private key, they will use their private key, and everyone will lose.
This community deserves better and those who encourage this practice at this point in time, with all we have learned, myself included, should be called out and chastised for their decision.
I feel this way partially because I wish someone had educated my ass earlier about the risks and what I was encouraging. My naivety was the cause of this decision. I failed to realize that entering private keys on websites trains users that it’s okay to enter their keys on websites. It also makes you a huge target for phishers, scammers, and hackers. Even sophisticated attacks that target the underpinnings of the internet.
In the past, we removed the ability for users to access their funds via private key on MyCrypto.com. For those who still want to use their private key in a more secure environment, we’ve made available the downloadable MyCrypto Desktop App.
This was a hard decision as it added friction to people’s experience and removed core functionality from our most-used product. However, the data and stories from people who had lost their funds made it clear that the benefits would outweigh the cost.
We hope that those building products in this space learn from our mistakes, take action to prevent further loss, and stop encouraging bad practices.

Recommended Methods of Keeping Yourself Secure
- MetaMask
- Hardware Wallet (Ledger, Trezor)
- EtherAddressLookup Chrome Extension
- Brave Browser
- The SIM-Swap Bible
- Security Guide For Dummies And Smart People Too